Major email providers including Google, Yahoo and AOL are set to tighten rules on incoming email – making accounts more secure against SPAM and demanding more of bulk senders who want to see their emails delivered.
Google and Yahoo alone represent more than two billion email accounts, many of them belonging to individual consumers for personal use. Estimates suggest around 70% of these have no protection against domain spoofing.
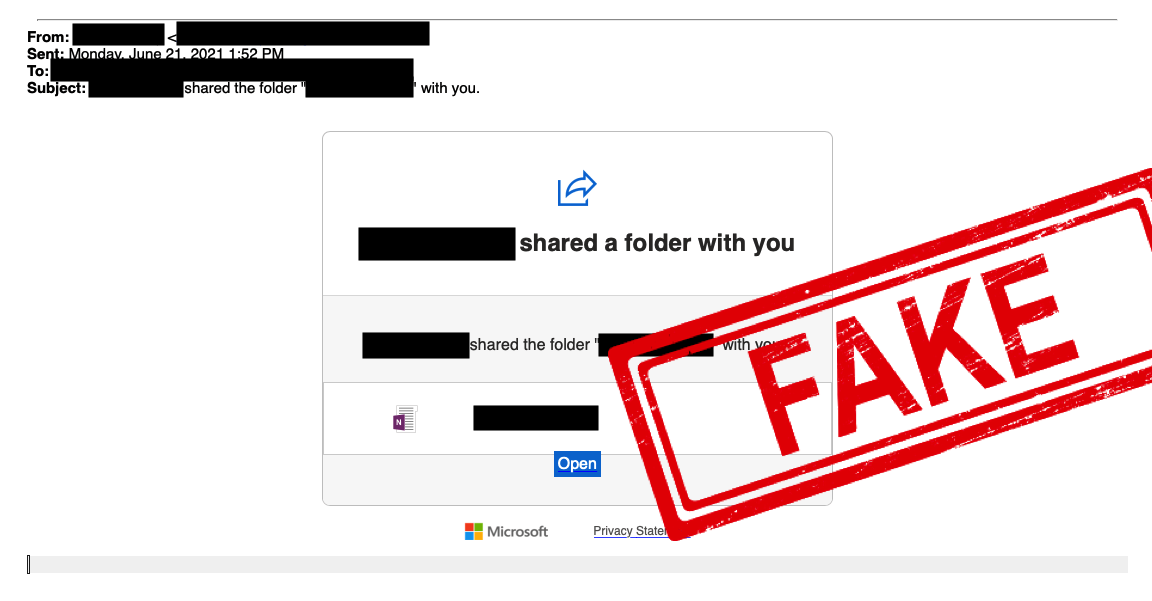
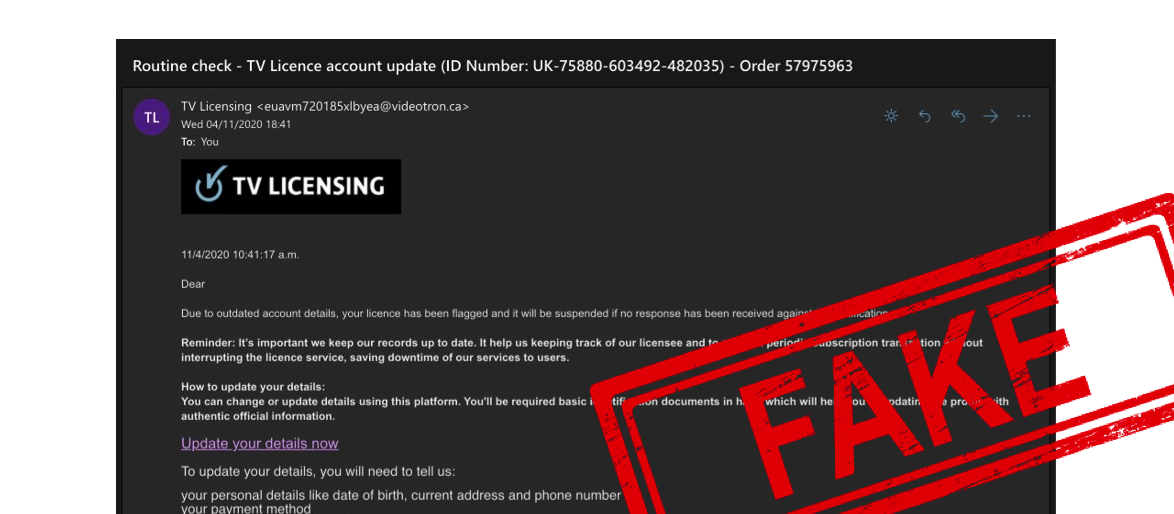
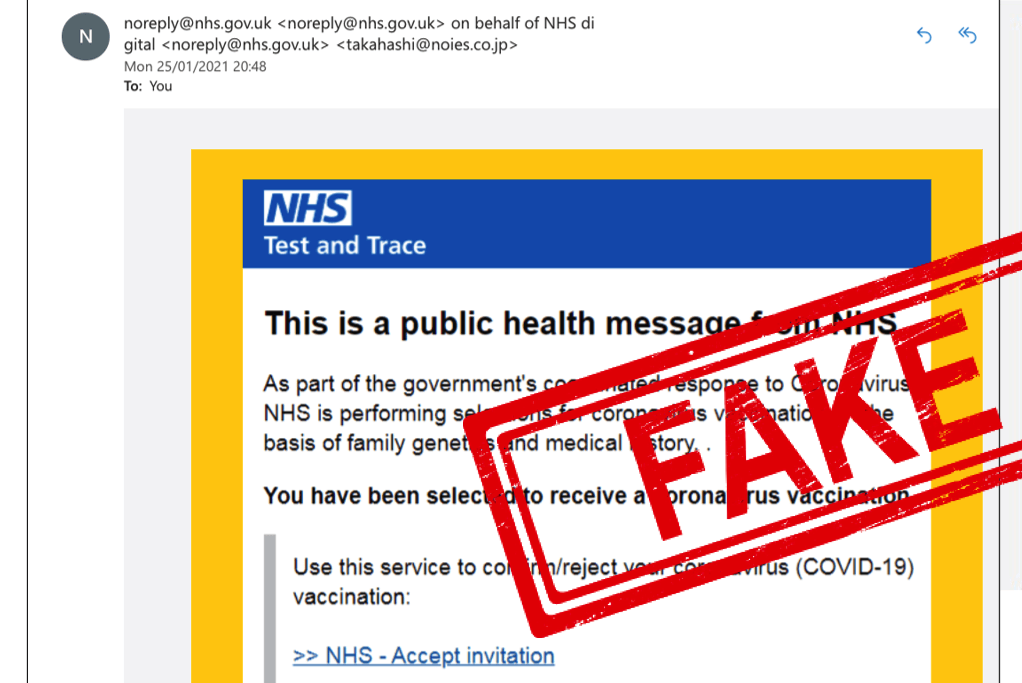
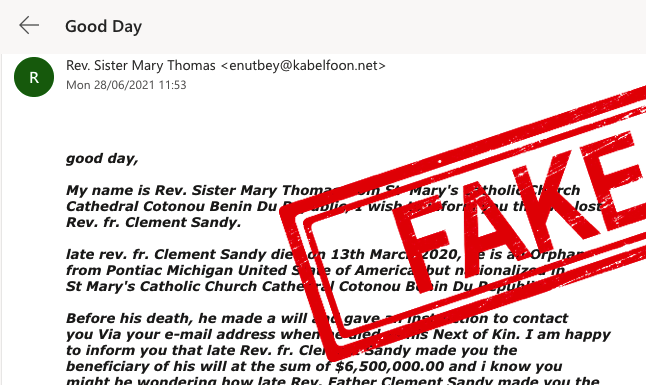
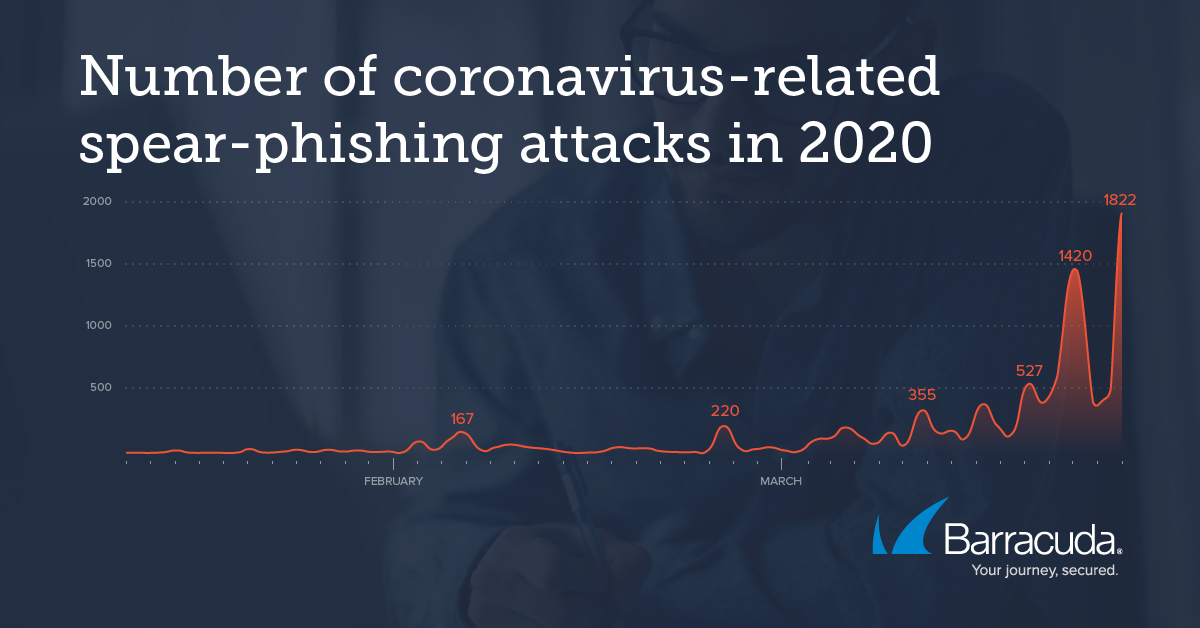
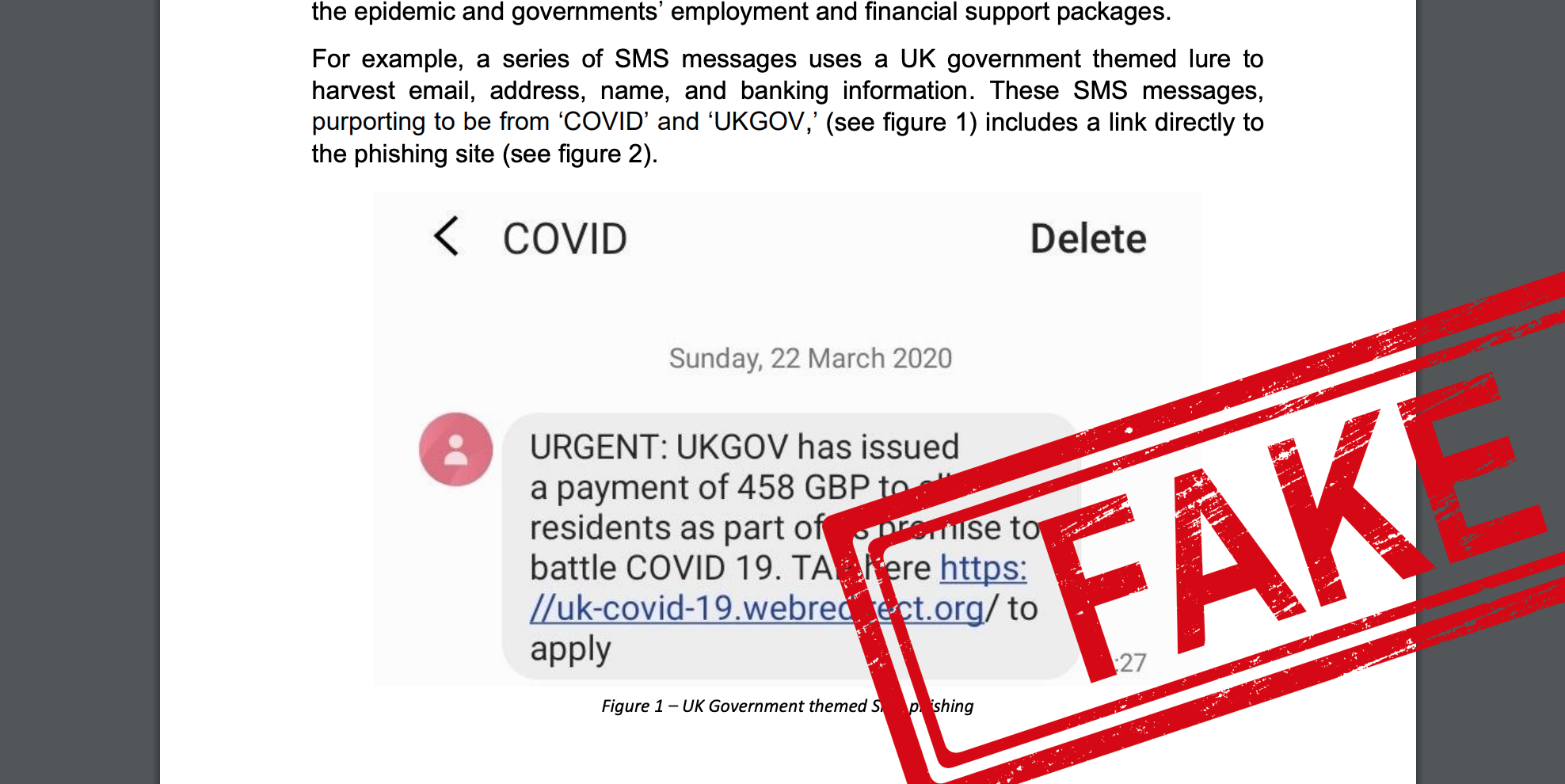
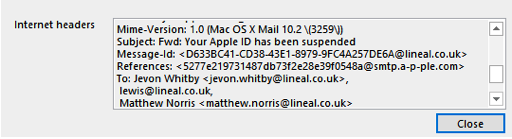
Until recently, even many basic security protocols such as SPF (checking whether email header and ‘sent from’ address match) were not enforced on major email platforms such as gmail – allowing fraudulent emails to unsuspecting users. This made phishing emails easier to circulate, harder to detect, and has been recognised as one of the biggest enablers for cyber security attacks.
DKIM – a protocol that signs both the real domain and email with a cryptographic signature that email clients can cross-reference for authenticity – is also often absent, with email providers increasingly looking to demand better standards from email senders.
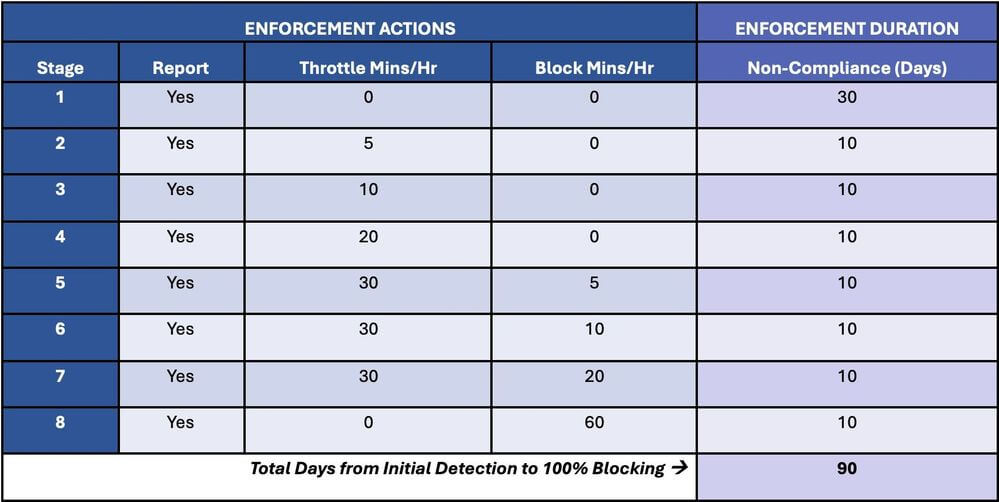
From February 2024, bulk email senders must adhere to the following requirements outlined by Google and Yahoo:
New Sender Rules
SPF & DKIM Enforced – Business and organisations that need their emails to be delivered safely will have to add SPF & DKIM settings to their domains and mail servers that verify whether emails purporting to be from them are genuine, and have not been tampered with. Without checks in place, Gmail and Yahoo may reject those emails altogether.
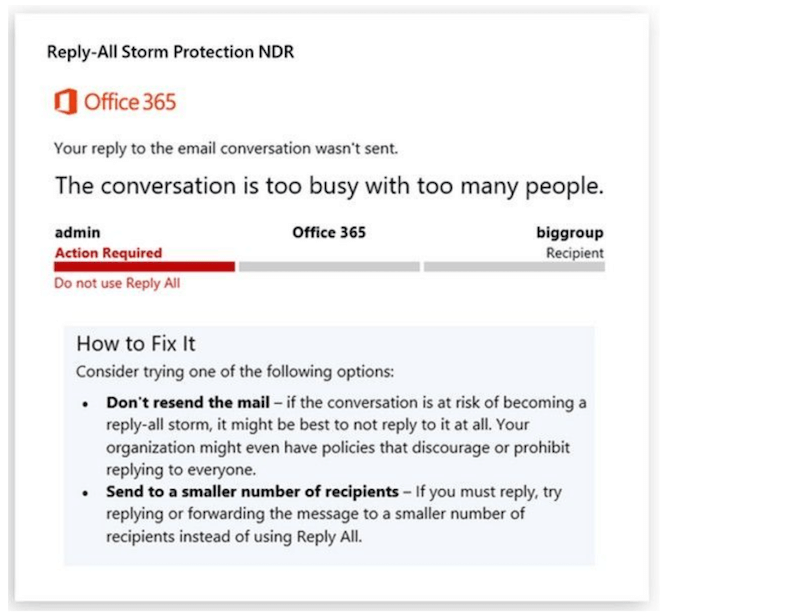
Easy Unsubscription – bulk emails must offer ‘one-click’ unsubscribe options for recipients, making it easy for email recipients to opt-out of repeated unwanted messages, and keep clutter under control.
DMARC, the most challenging of the requirements, will be enforced for bulk email senders sending more than 5,000 emails per day, aimed at preventing rapid phishing scams and other mass attempts at fraudulent communications.
For those communicating with the public, the changes are likely to prove crucial, and IT managers need to prepare carefully to ensure their emails continue to be trusted.
For Cyber Security assistance and expertise, please contact our team today.