Microsoft have altered how macros activate in Microsoft Office files, in an effort to improve users’ cyber security.
Macros, which allow office files to run sequences of commands, can be used to automate simple tasks – but also maliciously by hackers as a mechanism of attack.
Macro-based hacks have been around since the late 1990s, but remain surprisingly effective. Users are commonly asked to open unexpected email attachment and authorise the macro to see its mystery contents, allowing the macro to introduce malware onto the system. In effect, users authorise the hack themselves.
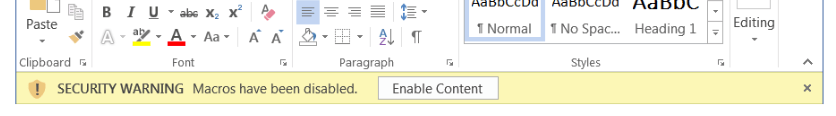
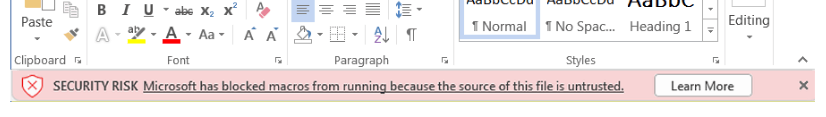
Instead of the old yellow ‘Security Warning’ labelled with an instant ‘Enable Content’ button users previously saw when using Microsoft Office applications, files will now prompt with a red ‘Learn More’ button, and users will be forced to see guidance on using macros securely, before being able to enable the content.
This small move – which was originally rolled out, rolled back, and then rolled out again – has been part of a slow clampdown on macros that has lasted more than two decades. Over the years macro functionality has steadily had more restrictions applied – in 2003 IT admins could require macros to have a trusted certificate (more like software applications) and as of 2013, could block macros by default.
But Microsoft hopes this simple firebreak will nudge us to think twice, and stop (potentially millions) of people from endangering themselves and their technology with a click.
Human nature continues to catch out many users curious about mystery documents – particularly since only a small fraction of Microsoft Office users are even aware of Microsoft 365’s powerful automation features.
For IT support and expertise, please contact our team today.