It’s 2021 but somehow the phishing email scams just keep coming.
You could almost miss the days when ‘Bill Gates’ would get in touch by email to offer you a shipment of diamonds. Modern email scams are much more sophisticated, the designs more convincing, and the payloads more dangerous – than ever.
Our advice remains the same:
- Be wary of any unsolicited email or unknown contact.
- Always look to see if an email is being sent from the correct domain.
- Don’t open any unexpected or mystery attachment, or click links to unrecognised destinations.
- If unsure, verify information with someone by asking via a communication method other than email (eg: by looking up a phone number separately from the email, and calling direct.)
Here’s our pick for some of the sneakiest our team have seen ‘in the wild’:
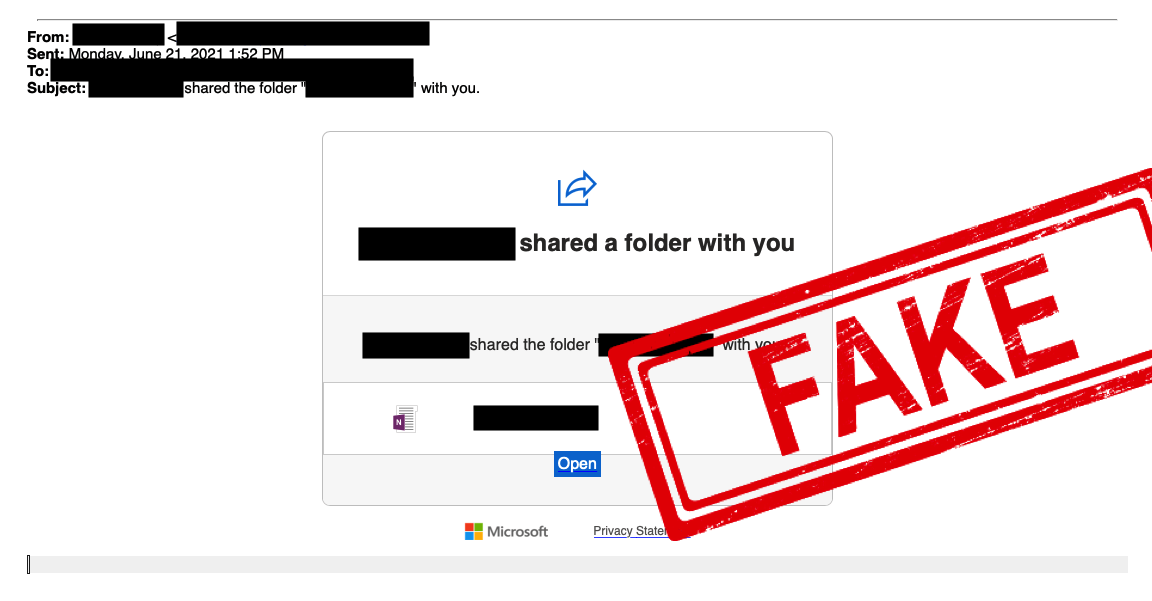
The Dodgy File Share (Deluxe Edition)
As useful as a crowbar in the arsenal of the burglar, cybercriminals have been using these ever since file sharing and collaboration apps took over the world – this one appeared even more persuasive for it’s nearly spot-on branding imitating a Microsoft 365 file share link.
But the Deluxe edition takes this scam to a whole new level – with just a mistaken click giving cybercriminals an automated account access, and even replying affirmatively to emails between users asking if these are genuine. Nasty.
 |
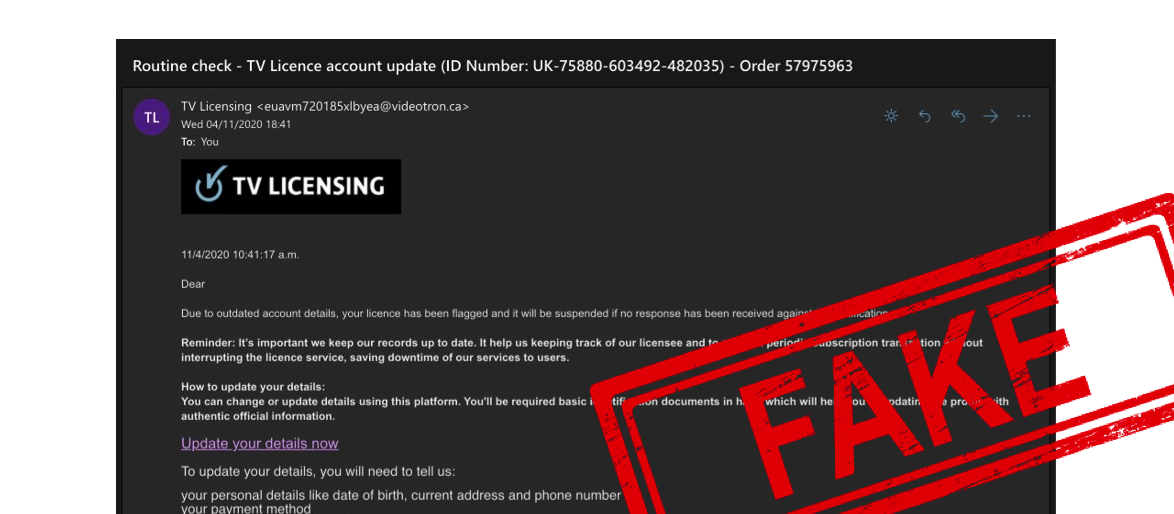
The TV License
TV licensing is something many people buy once a year, often never receiving physical proof, and don’t think about much – making this a clever way to steal card details without arousing too much suspicion.
These often go the extra mile – making up fake customer numbers and renewal dates – to seem real, which can also identify the email as a scam if cross-referenced in your own records.
 |
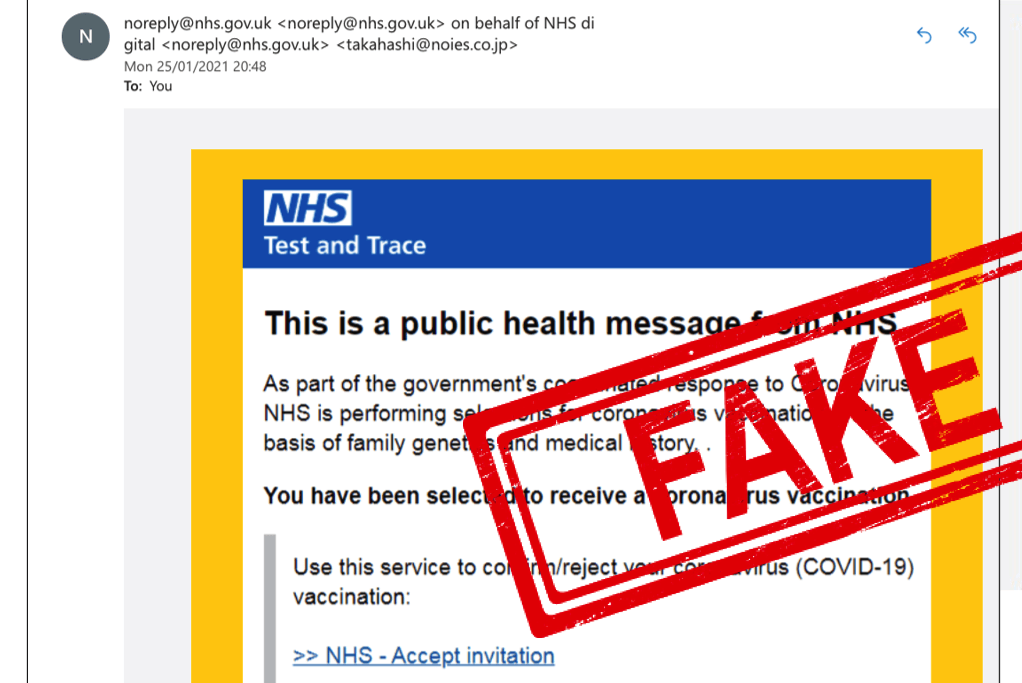
The Pandemic Phish
Cybercriminals don’t let little things like ethics get in the way of a good scam – with widespread public fear, and the NHS Covid vaccine roll-out in full swing, everything is an opportunity to hack accounts, steal information, or extort money.
Please be aware the real NHS will contact you via a combination of text message and/or post, and certainly won’t threaten you with the loss of your vaccine appointment if you don’t click a suspicious link.
 |
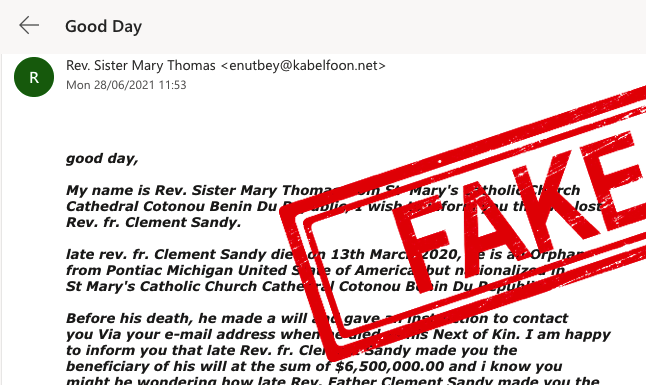
Divine Intervention
OK, perhaps not a threat to everyone – but it’s easy to imagine this inheritance scam prompting a click from someone more spiritually-minded. Technology aside, a compelling story is sometimes the most persuasive scam of all.
 |

For Cybersecurity expertise and support, please contact our team today.