Microsoft have announced plans to throttle, and eventually block, emails sent from on-premises and hybrid Microsoft Exchange Servers that remain unpatched.
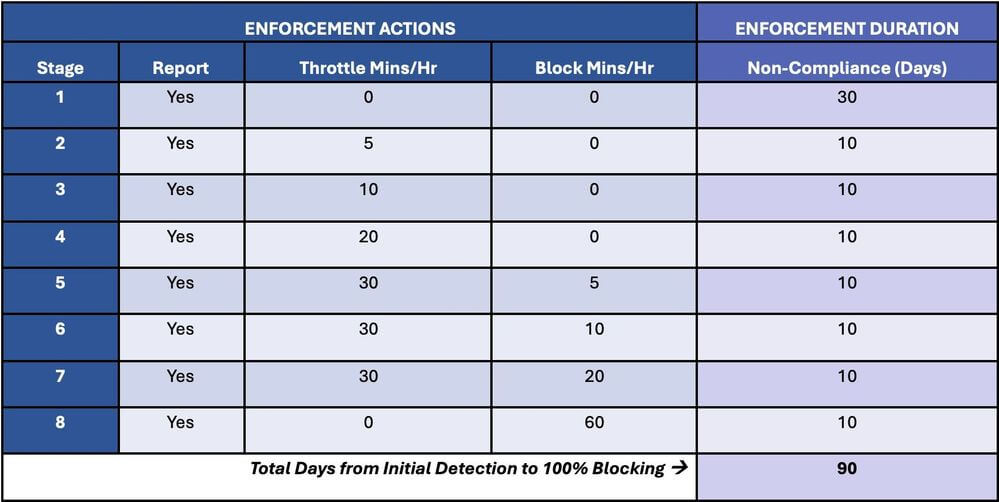
“Persistently vulnerable” servers will receive incrementally stricter controls, beginning with throttling (delayed delivery) up to and including a complete block beyond 90-days, preventing onward delivery to other Microsoft-based email accounts such as those in Microsoft 365/Exchange Online and Outlook.com.
The dramatic move puts yet another large question mark over organisations relying on on-premises Exchange server hardware. While Exchange 2003, 2007, and 2010 are now rare, Exchange 2016 still remains in surprisingly widespread use, and many copies of Exchange 2019 are not regularly patched against known vulnerabilities.
Extra controls will apply to servers that run on outdated or unsupported software or haven’t been patched against known security bugs – to help Exchange admins identify unpatched or unsupported on-premises Exchange servers, and allowing them a chance to upgrade or patch before they become security risks.
Recent times have seen a string of major vulnerabilities against Exchange server – including by the Chinese hacking group Hafnium.
Even in 2023, A simple Shodan search still shows thousands of Internet-exposed Exchange servers, with many still waiting to be secured against attacks targeting them with ProxyLogon and ProxyShell exploits, two of the most exploited vulnerabilities from 2021.
For cyber security advice and expertise, please contact our team today.