A good cybersecurity strategy includes layers of defensive counter-measures, designed to mitigate a wide range of threats at different levels of your organisation.
However there’s lots of ways you can help bolster your cybersecurity a little more, even working on a budget of (basically) zero – here’s our pick of the best:
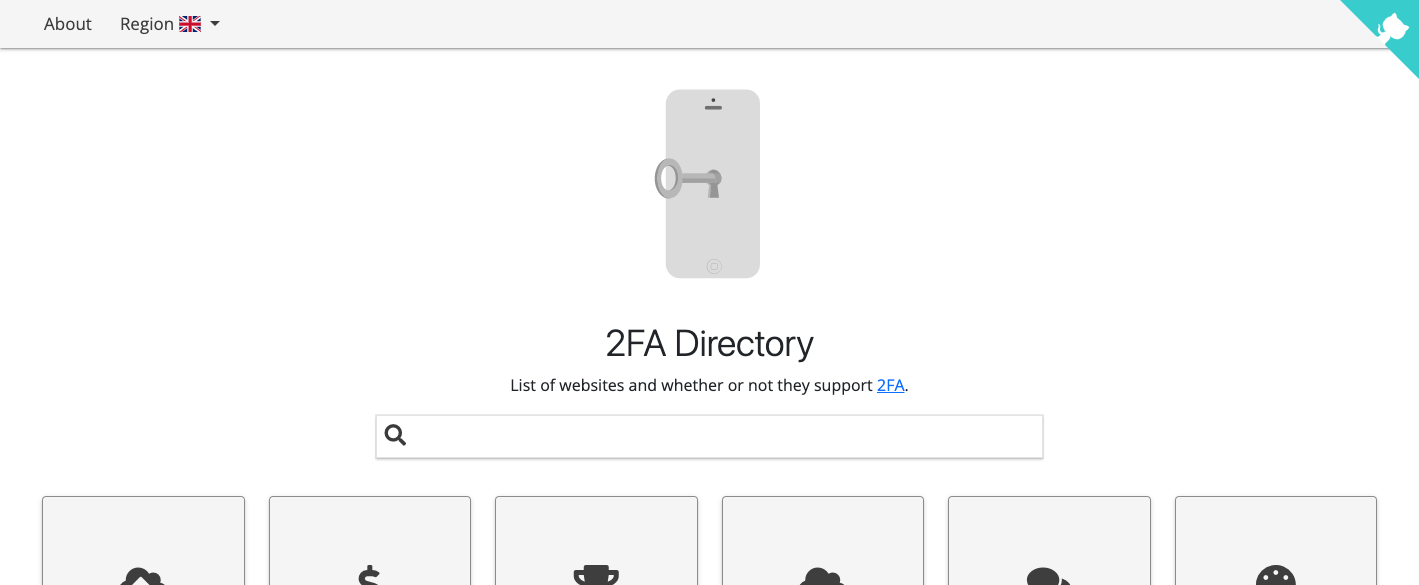
2FA / MFA Directory
We’ve written before about the colossal effectiveness of turning on multi-factor authentication for all your online logins – in particular the way it helps prevent an outside attacker accessing your technology remotely with stolen credentials.
Although compulsory for online banking in the UK, this feature is often available for free elsewhere online as well – and you should take full advantage.
This useful website is an index of websites and online services that already offer 2FA on your account(s), which methods are available, and where to find them.
Customised Login Pages
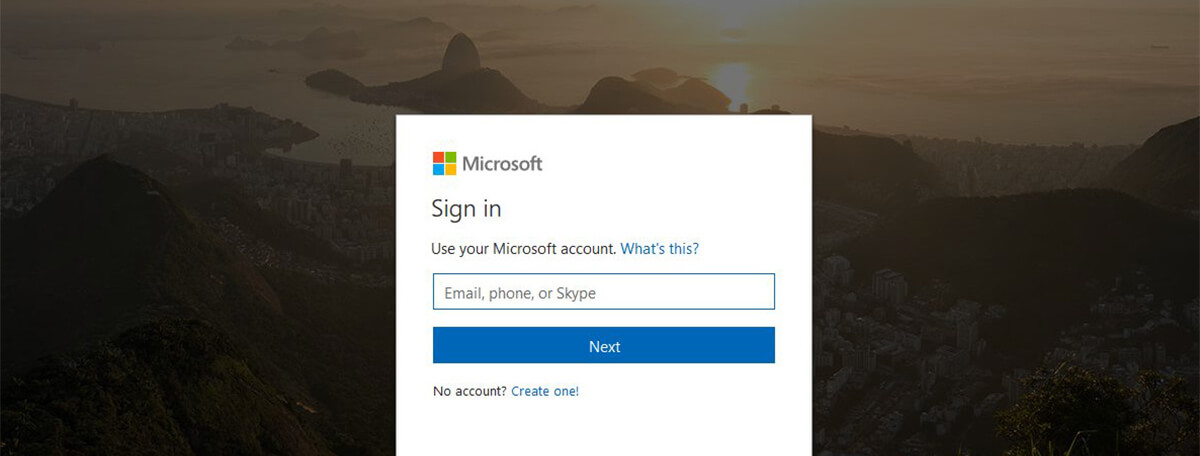
By default, your login window for many public cloud services is identical to everyone else’s – for example, by default Microsoft 365 companies see a picture of Rio de Janeiro each time they sign in. However, many people don’t realise this image can be customised, making the sign-in experience unique for your compny.
This feature is often free – but has one really important cybersecurity benefit: it helps your users realise when they might have been redirected to a phishing website. Fake login pages attempting to steal their credentials will often use the default background image to be recognisable to more people, rather than your custom one. When one of your staff clicks the wrong link, the wrong background might just help alert them before they hand over their credentials to a cybercriminal.
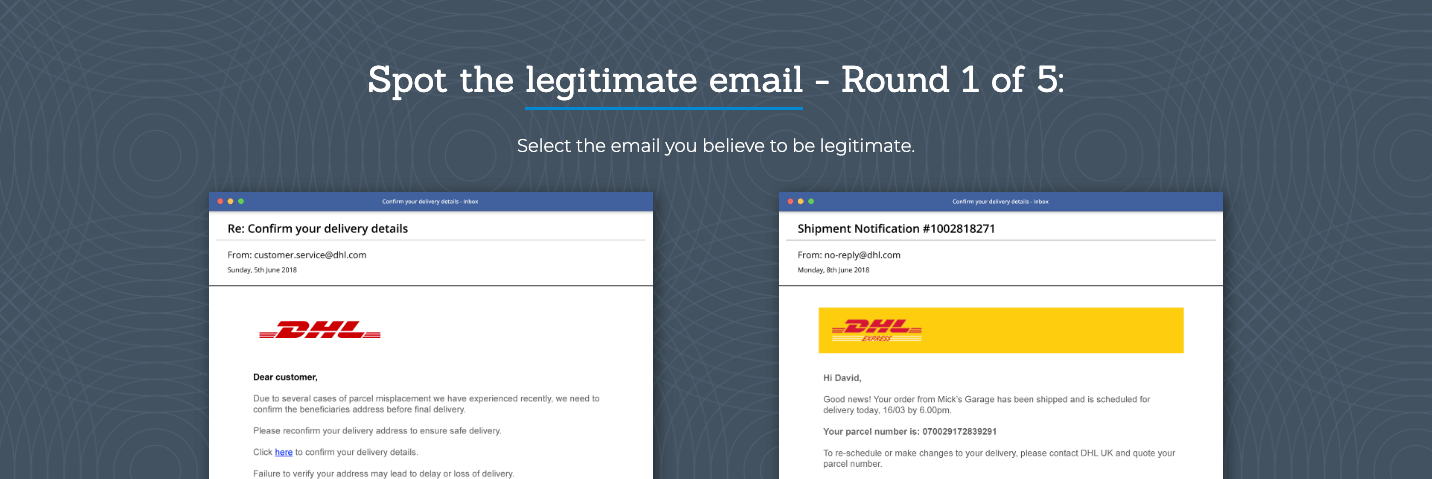
‘Spot the Phish’ Quiz
Let’s be honest, many online cybersecurity training tools are a bit rubbish – but this little gem of an online game from email security provider Barracuda uses five real examples of scam emails (A & B) to quiz your staff, and educate them on the warning signs.
User training helps build a resilience to cybersecurity threats that isn’t available via technology – protection for the ‘human layer’ of the organisation that needs to be vigilant, no matter which technology they’re using. Challenge your team today!
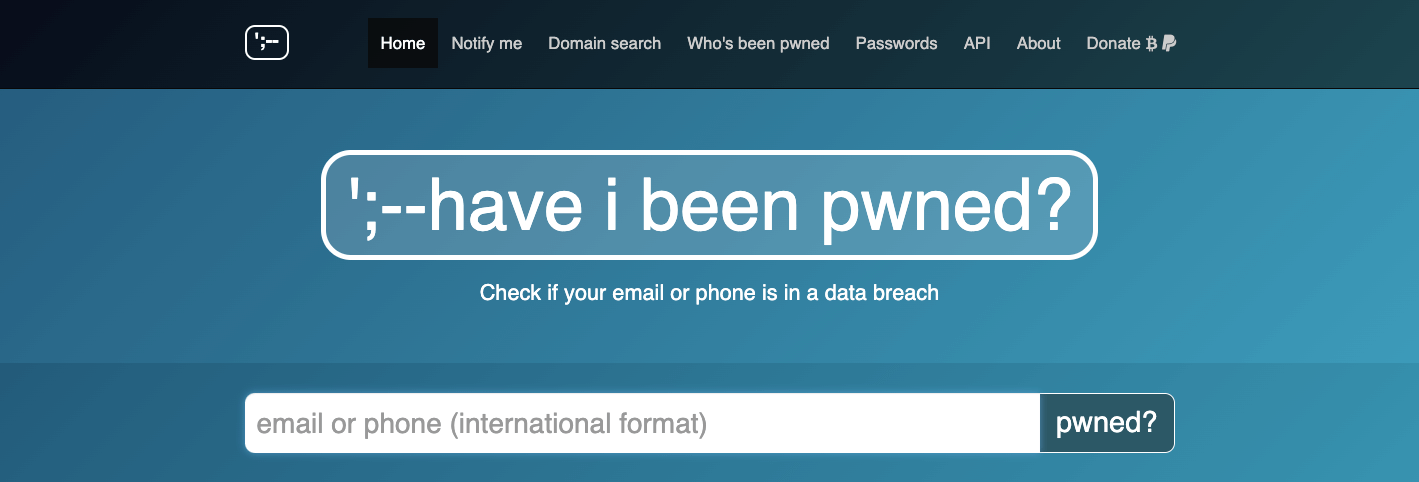
Has your Email been Pwned?
This delightfully terrifying website allows you to search those massive cybersecurity breaches you read about in the news for your own email address – informing you whether your information was involved, and where.
If you find an old email address has been listed in a known data breach, it’s best to update your password, turn-on two-factor authentication, and make sure your haven’t used that password anywhere else online – because it’s entirely possible that your credentials are already circulating as part of large stolen data dumps on the dark web.
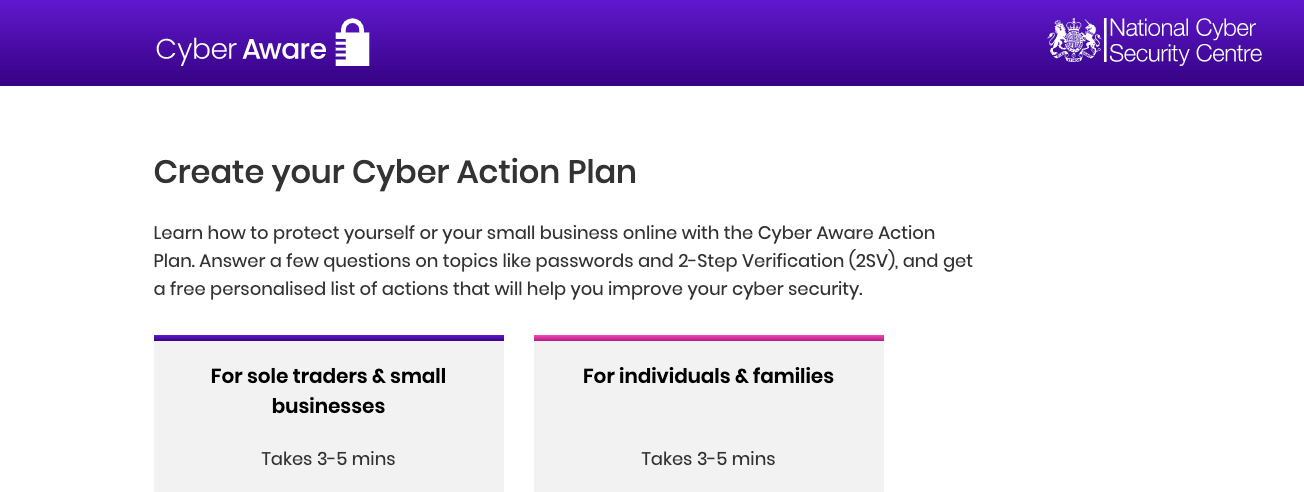
Build a Cyber Action Plan
The UK National Cyber Security Centre (part of GCHQ offers a free ‘Cyber Action Plan’ tool to sole traders and smaller businesses that takes you through a short questionnaire about your business to help you build a starter list of recommendations to consider.
This is a similar exercise to that undertaken by professional managed cybersecurity providers – but on a smaller scale – well worth a look!
For cybersecurity expertise and support, please contact our team today.