V.1.2, Download PDF (UK)
‘You’ve Been Hacked’ copyright (c) Lineal Software Solutions Ltd 2023.
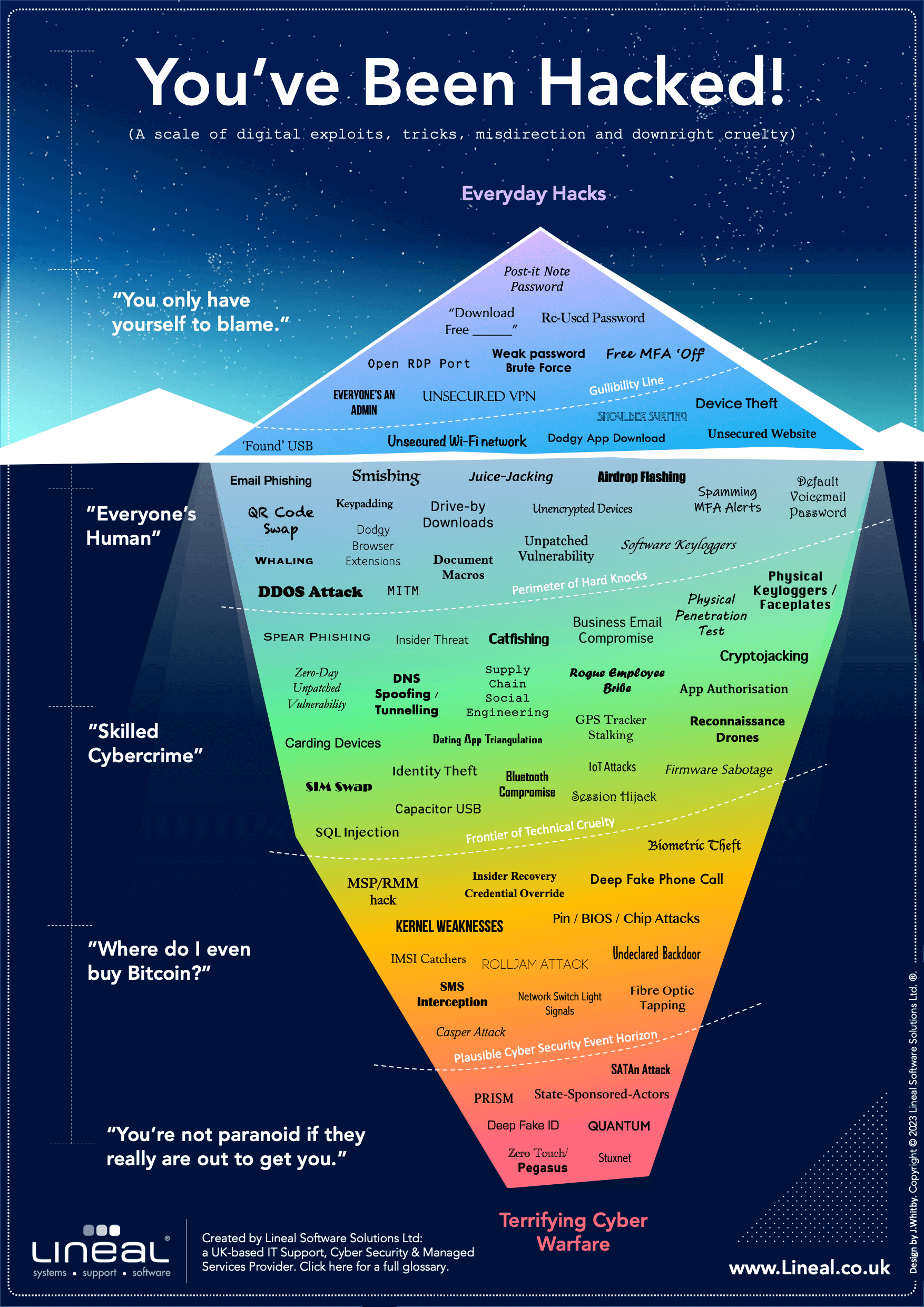
Cyber Breaches Glossary
| Airdrop Flashing | Maliciously using pre-shared files (such as thumbnail images) supported as part of wireless sharing technology to send unwanted images to unsuspecting users. First made infamous by ‘cyberflashers’ on the New York Subway. |
| App Authorisation | Malware or a phishing attack that tricks users by asking them to grant permission to malicious bolt-on apps. |
| ASCA | ‘Acoustic Side Channel Attacks’ gather audio signals such as keystrokes, fan noises and similar using malware on a secondary device in close proximity, which has a compromised microphone. Experiments suggests keystrokes can already be interpreted with 95% accuracy. |
| Business Email Compromise | A scam where attackers impersonate an executive or employee to trick companies into making fraudulent financial transfers. |
| Bluetooth Compromise | Attacking Bluetooth-enabled devices wirelessly to steal data, install malware or take control of the device. |
| Capacitor USB | A specially-modified USB memory stick containing a large internal capacitor that destroys the electronics of any system it is plugged into. See also ‘LetterBomb USB’. |
| Carding Devices | Card cloning techniques used to steal credit card information, typically from point of sale (POS) systems. More common in the early 2000s when card swiping was necessary to transact. |
| Casper Attack | Theoretical, but demonstrated to be possible – this uses a malware that generates signals via high-pitched, inaudible audio to remove data from even air-gapped computers. |
| Catfishing | A form of social engineering where an attacker creates a fake identity to lure a victim into a relationship or scam, often romantically. Common to social media. |
| Cryptojacking | Using someone else’s computer resources to mine cryptocurrency without their consent or knowledge, via hidden software or code embedded within web pages. Made infamous by the invention of Monero. |
| Dating App Triangulation | A form of stalking where an attacker uses distance information from multiple dating app accounts to triangulate the position of other users. |
| DDOS Attack | Using huge volumes of traffic to overwhelm websites and web services, making them unavailable for other users. Typically involves the use of botnets comprised of large numbers of infected PCs or IoT devices. |
| Deep Fake ID | The stuff of cyber security nightmares. Creating a fake biometric identity using deepfake technology to impersonate someone else or gain access to secure accounts or resources. |
| Deep Fake Phone Call | Using deepfake audio technology to create a fake voice and make a phone call impersonating someone else. See also: ‘Virtual kidnapping’ scams. |
| Default Voicemail Password | A hack based on accessing a user’s voicemail inbox remotely by trying the phone manufacturer’s default voicemail password to see if the user has left it unchanged. Often described as ‘phone hacking’ in the UK following a major court case against News International between 2010-2014. |
| Device Theft | Stealing physical devices such as laptops, smartphones, and tablets. May sometimes involve removing storage components, such as hard drives, from the device itself. |
| DNS Spoofing/Tunnelling | Manipulating the DNS system to redirect users to fake websites or intercept traffic. |
| Dodgy App Download | Apps downloaded from untrustworthy sources that may contain malware or steal user data. Can also refer to imitation apps smuggled onto reputable app stores for unsuspecting users. |
| Dodgy Browser Extensions | Malicious browser extensions for customisable web browsers that can redirect user data or inject ads. |
| Document Macros | Malicious macros embedded in documents used fetch and run malware when the user approves the macro. Commonly exploits Microsoft Office file types, but has faced a steady clampdown from Microsoft over the years. |
| Download Free ______ | A common tactic used by attackers to trick users into clicking links to fake free content or media. Click here for a free iPod! |
| Drive By Downloads | Automatically downloading forms of malware without the user’s knowledge or consent via a visit to a website that auto-runs certain code. |
| Email Phishing | Sending fraudulent emails that appear to be from a legitimate source to trick the recipient into disclosing sensitive information or downloading malware. Often combined with special phishing websites designed to trick users out of login credentials or more complex data. |
| Everyone’s an Admin | The danger posed by giving standard users administrator privileges, making it easier for attackers to take full control of systems later. Now disallowed under UK Cyber Essentials Framework. |
| Fibre Optic Tapping | Tapping into fibre optic cables to intercept and steal data. |
| Firmware Sabotage | Altering the firmware on devices to install malware or gain control of the device. May occur as part of compromised supply chains. |
| Found USB | Leaving a USB device in a public place to trick people into using it. May contain malware. A common part of targeted scams on institutions. Demonstrated to be terrifyingly effective. |
| Free MFA ‘OFF’ | The risk posed by a user declining to enable Multi-Factor-Authentication, even when it is offered free of charge. |
| GPS Tracker Stalking | Using planted GPS tracker devices, to track individuals private location without their consent. |
| IMSI Catchers | Using a fake cell tower technology to intercept and collect data from mobile phones. Illegal in some countries, but proven to be available for purchase and use (or misuse) within certain sectors, such as policing and counter-terrorism. |
| Identity Theft | Stealing someone’s personal information to leverage access to other accounts, commit fraud or other crimes. |
| Insider Recovery Credential Override | An attack where an insider accesses internal company controls to override the stated recovery credentials of a user to grant a mechanism for access to a third-party. |
| Insider Threat | An attack where an insider with authorised access to a system intentionally causes harm themselves. |
| IoT Attacks | Attacks targeting Internet of Things devices such as smart thermostats, security cameras, and home automation systems. Commonly exploits poor quality device-level security or encryption on low cost devices. |
| Juice Jacking | Sabotage of public charging stations to compromise devices via USB. Often publicised, but not viable on locked iOS & Android devices since 2013. Some doubt over whether non-targeted juice jacking has ever been deployed outside of research environments. |
| Kernel Weakness | Exploiting a vulnerability several layers of abstraction lower, in the kernel of an operating system, to gain control of a system. |
| Keypadding | Checking for signs of physical wear on keys and other input devices to reverse-engineer passcodes – typically for number keypads with short passkeys, leading to few combinations. |
| MITM / ‘Man-in-the-Middle’ | Intercepting and altering communications between two parties to steal information. |
| MSP/RMM Hack | An attack targeting IT Support/Managed Service Providers (MSPs) or Remote Monitoring and Management (RMM) systems, used to gain privileged access to many clients’ networks and devices simultaneously. Infamous examples include Solarwinds Orion and Kaseya. |
| Network Switch Light Signals | Niche but technically possible – an attack method used on devices with no visual interface, such as network switches, allowing an attacker to access data based on the blinking patterns of status indicator lights. |
| Open RDP Port | A Remote Desktop Protocol (RDP) port that is open and available, potentially allowing unauthorised access to the device or network. |
| Physical Keyloggers / Faceplates | Devices such as cameras, fake ports or physical overlays attached to a keyboard or other input device, used to capture keystrokes and obtain login credentials or other sensitive information such as card details. Often targets ATMs. Also known as ‘Skimming’. |
| Physical Penetration Test | An ‘in person’ attack on a physical facility to identify vulnerabilities in security measures. Often relies on impersonating real personnel to access restricted areas or smuggling compromised hardware onto the network. |
| Pin/BIOS/Chip Attacks | Techniques used to exploit vulnerabilities in a device’s PIN, BIOS or chip to gain unauthorised access. Often requires specialist hardware or electronics expertise. |
| Pegasus | A highly sophisticated example of ‘Zero-Touch’ spyware developed by the Israeli ‘NSO Group’, used to infiltrate mobile devices and extract personal data. Officially just for policing and counter-terrorism use, Amnesty International and others argue the software has been used to target journalists and political opponents of undemocratic regimes. |
| Post it Note Password | A password written down on a physical note, which can be easily lost or stolen, potentially leading to unauthorised access. Particularly disastrous when attached to the device it refers to. |
| PRISM | A mass surveillance program on internet traffic run by the US National Security Agency (NSA) – used to collect internet communications from a wide range of sources, including the back-end systems of many major tech providers that form the backbone of the internet itself. |
| QUANTUM | An attack-suite of special tools developed by the US National Security Agency (NSA) – whereby a compromised router is requested to access both a legitimate website and a pre-prepared second web server in a very small time frame, introducing code into an exploited browser before the first web server has time to respond. Alternatively known as a ‘Man on the Side’ Attack. |
| QR Code Swap | A scam that involves replacing legitimate QR codes with fake ones, leading to a malicious website or app. |
| Reconnaissance Drones | Drones used for intelligence gathering to conduct aerial reconnaissance on a target or spy using unexpected camera angles. |
| Re-Used Password | The danger caused by using the same password for multiple accounts, leading to further security breaches when one account is compromised. |
| Rogue Employee Bribe | A method of gaining unauthorised access to sensitive information or systems via bribes or blackmail against those with privileged access. |
| Rolljam Attack | A wireless car key fob-based compromise that allows a hacker to intercept the encrypted signal from the key fob and access the car. |
| SATAn Attack | Theoretical but shown to be possible – a hacking method based on transmitting data from the electromagnetic signals generated from wiring such as SATA cabling. |
| Session Hijack | An attack where an bad actor takes control of an active session between a user and a web server, allowing the attacker to perform unauthorised actions on the user’s behalf. |
| Shoulder Surfing | The act of overlooking a user to steal access credentials as they are typed. |
| SIM Swap | An attack that involves gaining access to the mobile number of a user, often via a porting request to a mobile provider, allowing the attacker to complete a second compromise such as a bypass of SMS-based multi-factor-authentication (MFA). |
| Smishing | A phishing attack conducted via SMS or text messages, attempting to trick the user into clicking a link or giving up sensitive information. Can be used to deploy mobile-specific malware. |
| SMS Interception | Various methods of rerouting SMS-based communication as a way of accessing private information. |
| Software Keyloggers | Malware that records keystrokes on a device, allowing attackers to obtain login credentials or other sensitive information. |
| Spear Phishing | A highly targeted phishing attack, usually involving emails that appear to be from a trusted source, aimed at a specific individual or very specific group. |
| SQL Injection | An attack that targets web applications by injecting malicious SQL code into input fields, allowing the attacker to access or modify the database. Has led to large-scale card detail thefts on major online providers, such as airlines. |
| Spamming MFA Alerts | An attack that involves overwhelming a user with multiple MFA (multi-factor authentication) alerts, sometimes at unusual times, hoping the user will eventually approve one without verifying it properly. |
| State-Sponsored-Actors | Dedicated individuals or groups sponsored by a government to carry out cyberattacks, espionage, or other malicious activities. |
| Stuxnet | Not strictly a hacking technique, more of an example of just what is possible – A device-specific computer worm distributed via targeted USB drops that only activates to damage the industrial control systems of nuclear facilities in Iran. |
| Supply Chain Social Engineering | An attack that targets the supply chain or third-party vendors of an organisation to gain unauthorised access or introduce malicious instructions such as changes to payments. |
| TEMPEST Attacks | A method of stealing data in the form of electromagnetic radiation from the logic board of a compromised air-gapped computer using a GSM receiver placed nearby (eg: in a mobile phone.) |
| Thermal Imaging | A method of stealing data from a compromised air-gapped computer using thermal imaging of key components whose temperatures can be calibrated to transmit coded signals via radiation. |
| Undeclared Back Door | A hack based on exploiting a ‘back-door’ added secretly by the manufacturer of a product or service, that has not even been disclosed to the public. |
| Unencrypted Devices | Devices that do not use encryption to protect stored data, making it vulnerable to unauthorised access if lost or stolen. |
| Unpatched Vulnerability | A security flaw in a software or system that has not been fixed by a software patch or update, even if one is available, leaving the system vulnerable. A 2015 survey by Verizon suggests more than 90% of all unpatched breaches happened more than a year after the original vulnerability was published. |
| Unsecured VPN | A Virtual Private Network (VPN) that lacks proper security measures, leaving it vulnerable to hackers and unauthorised remote access to a network. Believed to be the cause of the crippling attack on Colonial Pipeline in 2021. |
| Unsecured Website | A website that does not have adequate security measures in place, such as encryption between web server and user, allowing it to be vulnerable to cyberattacks and man-in-the-middle attacks. |
| Unsecured Wi-Fi Network | A Wi-Fi network that is not password-protected or uses a weak password, making it an easy target for cybercriminals to intercept and steal sensitive data, or get heightened visibility of other users. A major risk of free ‘public’ Wi-Fi networks. |
| Weak Password Brute Force | A technique used by hackers to guess a user’s login credentials by systematically trying out different combinations of usernames and passwords until they find a match. Usually automated, making approximate password strength calculable. |
| Whaling | A type of phishing attack that targets high-level executives or individuals with access to more resources or more sensitive data. |
| Zero-Day Unpatched Vulnerability | A vulnerability in software or hardware that is unknown even to the manufacturer or software developer, leaving it unpatched and exploitable by hackers for an unknown period of time, and difficult to guard against for the end user. |
Let’s Talk Cyber Security:
Lineal are an ISO 9001/27001 accredited and Cyber Essentials Plus (CE+) certified Managed Cyber Security provider.
Get in touch with us today for a confidential, no-obligation conversation about your cyber security options – it might just make all the difference.
Contact us:
|
Read our Privacy Policy. This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.