Each year GCHQ’s National Cyber Security Centre issue stricter new rules for business and organisations looking to secure UK Cyber Essentials (CE) and Cyber Essentials Plus (CE+) Certification.
Continuing themes from last year, there are now tighter rules on account access, thin clients, device firmware, remote desktops, antivirus/EDR solutions and more. Despite the success of the Cyber Essentials scheme, the past year has seen some notable cyber attacks on British organisations, and renewed calls for cyber security vigilance.
We’ve compiled a summary to help organisations prepare for what revisions are coming down the line in April.
Multi-Factor or Else.
Even sooner than many expected, Cyber Essentials will now require not only Administrators to have Multi-Factor Authentication enabled – but all end-user accounts as well, across all platforms. Previously exemptions were granted for services without this option available, now that gap closes.
Instead, where a service doesn’t support MFA this will now be declared a non-conformity, bringing digital services fully into line with the rules enforced on UK online banking, and even applying to school children – right down to reception-age.
That’s likely to pose a challenge for companies (and particularly schools) using any software or web services which don’t yet offer MFA – so many organisations may need to look at augmenting their IT setups with 3rd-party MFA solutions like Cisco Duo.
Don’t forget the Firmware!
Software version controls now extend to hardware device firmware – with the definition clarified to specifying “firewall and router firmware” in particular – which was always essential, given the perimeter nature of these devices. In a rare step back, firmware on servers, PCs and other devices has been removed from the scope.
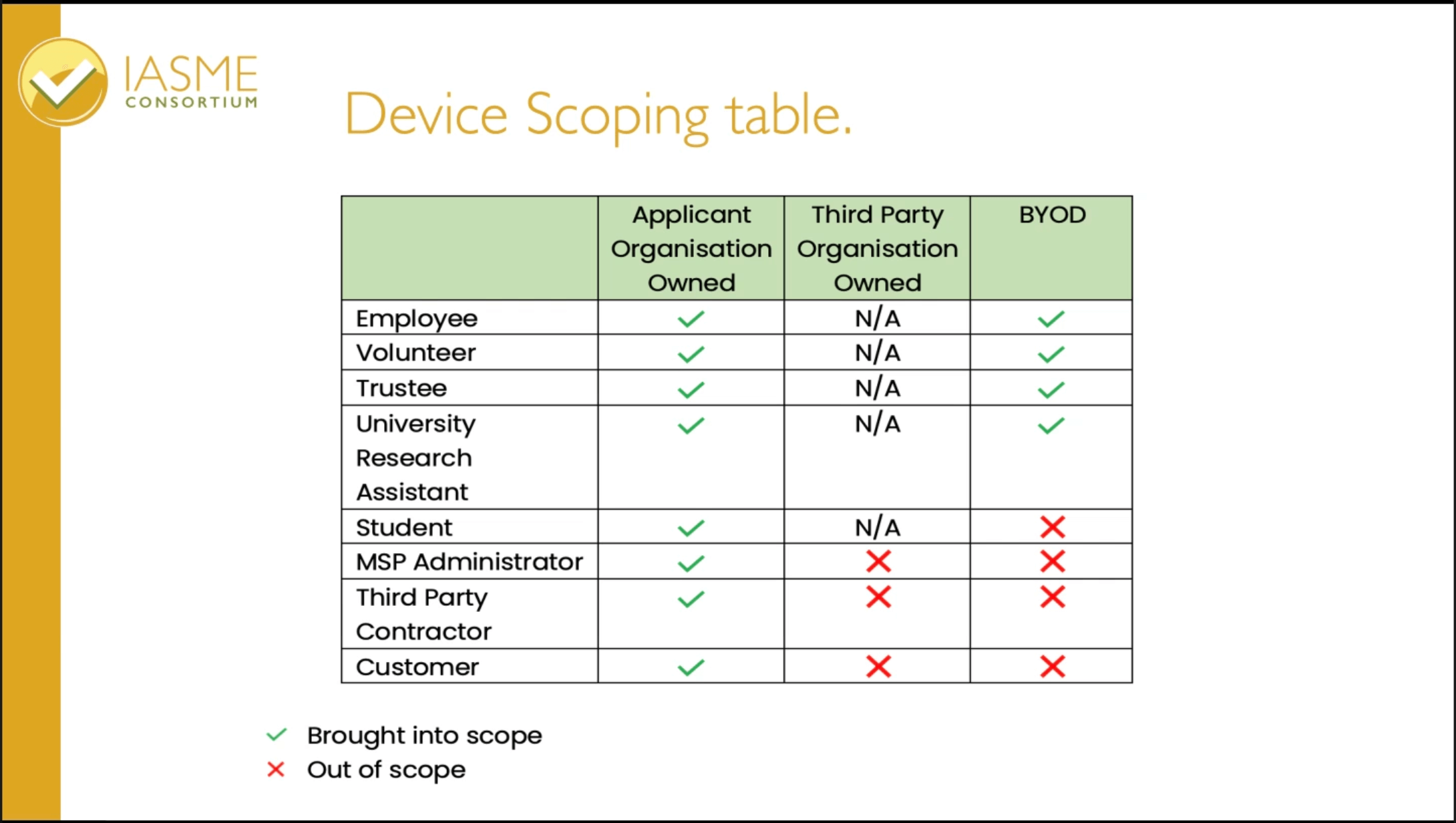
Device Clarifications
The NCSC has admitted third-party devices have been a point of confusion – and has published a revised table clarifying which devices are within the scope of Cyber Essentials. Updates will apply only to devices which are not domain-joined, or when unlocked have limited access to data (smartphones, handheld scanners etc.) If the a vendor does not allow configuration to see CE standards, the application may use the vendor defaults without incurring a non-conformity.
Given that the definition partly rests on who owns the device in question, we predict more changes in future years.
Not Just Any Anti-Malware
Antivirus solutions no-longer need to be ‘Signature-based’ – since the best EDR solutions don’t rely on signature-based detection of threats anyway. CE+ audits will include extra tests to verify that anti-malware software is effective (beyond simple EICAR tests) and application allow-listing is being encouraged.
Scoring Changes
Minor/Major non-conformities have been merged with a single Non-Conformity mark. Any applicant receiving three non-conformities will receive an instant failure. Corrective actions must now be completed within two days, despite some exceptions are available for larger organisations.
However, unsupported operating systems become an unfortunate immediate triple-word score: the presence of any unsupported operating system within the scope is an automatic fail.
For Cyber Security and Cyber Essentials expertise, please contact our team today.