Just occasionally cybercriminals discover a new technique for tricking users or gaining access to something they shouldn’t have.
Hacks and scams go in and out fashion like much else – depending on their effectiveness and particularly, awareness among the wider public.
It’s helpful to keep one step ahead, so here’s our pick of some newer emerging threats to watch out for:
MFA Fatigue
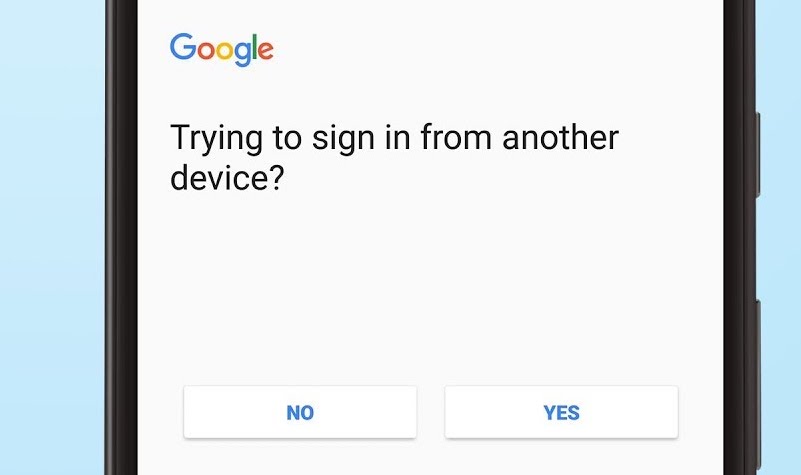
The introduction of Multi-factor ‘Prompt’ notifications on Android and iOS are meant to make life easier. Instead of typing in a six digit code sent by text or generated by an authentication app, the user simply clicks ‘Yes this is me’ (or similar) when prompted on their authorising device.
But a hacker who obtains your password may have the option to spam the user with such notifications, until the user either accepts one by mistake or deliberately to make the prompts go away.
This trick can even get the hacker past otherwise bulletproof MFA on an account by pestering a targeted user – and users are often spammed in the early hours, when they’re likely to approve the login attempt without thinking, believing it to be a technical fault. By the time they’re asleep again, the hacker has remotely accessed their account.
30 Pieces of Silver
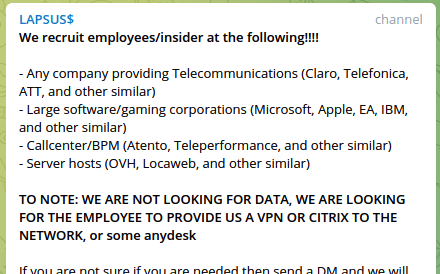
One of the most interesting revelations from recent arrest of members of the Lapsus$ ransomware group was wider publicity of their public-facing telegram channel.
Among the techniques used by the prolific hacking group were appeals to recruit disaffected employees of notable companies.
This presents an interesting strategic question: how do you defend against a disgruntled member of your team being bribed to hand over vulnerabilities, credentials or privileged access that would otherwise remain guarded? Attackers who begin inside a networks usual defences have an extra capability for ‘lateral’ attacks that use each system or login captured to slowly compromise more of an organisation.
An ‘Insider’ attack is perhaps a corporation’s worst nightmare – with even a single VPN or admin password able to cause severe damage.
Dodgy App Permissions
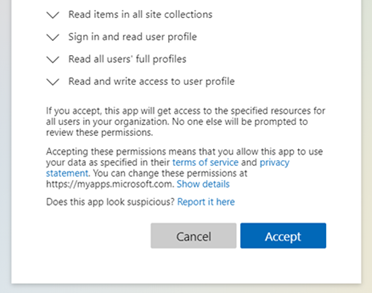
A massive ecosystem of additional connected apps is available for Microsoft 365 – although many require addition permissions (such as access to emails, calendars, contacts and more) which are approved through an authorisation standard called Oauth.
Unfortunately this is open to abuse, particularly ultra-targeted spear phishing of upper-level management and those with privileged accounts. First step: get the user to visit a URL that wants permission for an innocent-sounding app to connect with Microsoft 365. Second step: when the user ‘Accepts’ an app’s access conditions, they grant an access to much of their Microsoft 365 account – an access that works remotely without being re-authorised by MFA or any of the usual protections, often in perpetuity.
In some cases the permission windows for the suspicious app are specially modified so that cancelling is circular, or give the app immediate permission to email other users the same app authorisation to spread the hack further.
QR Codes
We’ve written before about the problem with QR codes – and many of the ways they’re potentially open to abuse.
In a mobile-first world, QR codes in public places can all too easily be tampered with to make users pay the wrong website, share malicious links on social media, or even dial premium numbers. Although Google Lens and similar apps will preview a link before the user clicks it, the underlying flaw is how easy it is to mimic the style and placement of official, legitimate QR codes, without the end user realising the swap has taken place.
The central problem is user awareness – would you click on a blind link in an email? No, exactly.
For cybersecurity expertise and support, please contact our team today.